Reston, VA (April 13, 2020) – Digital Hygiene for Remote Work during COVID-19
Cybercriminals have been active & creative at exploiting the COVID-19 pandemic for the various scams and attacks they carry out. In addition to washing your hands to prevent the spread of COVID-19, please be vigilant to follow your digital hygiene habits, as well.
Here are some Remote work Security Guidelines.
1. Antivirus
Make sure your Antivirus Application is Activated in your laptop (or Install an Antivirus application if you don’t already have one).Open your application by clicking the Start button in the lower left corner of your PC. In the search box, type the name of your Antivirus Software. Do a Full scan of your computer.(at least once in 15 days)
2. Avoid Unsecure or Public Wi-Fi
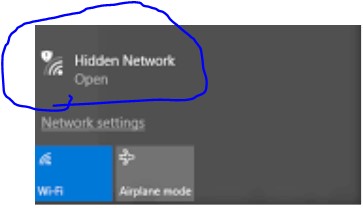 Do not use unsecure or public Wi-Fi for official purposes. Hackers can also use an unsecured Wi-Fi connection to distribute malware. If you allow file-sharing across a network, the hacker can easily plant infected software on your computer.
Do not use unsecure or public Wi-Fi for official purposes. Hackers can also use an unsecured Wi-Fi connection to distribute malware. If you allow file-sharing across a network, the hacker can easily plant infected software on your computer.
3. Secure Home Wi-Fi
Make a complicated Wi-Fi router password
Make your password a random sequence of letters, numbers and special characters, mixing uppercase and lowercase so no one could ever remember it. Fortunately, once a password is successfully entered into a device, it is not visible, so the people you give it to won’t be able to read it off to tell someone else. Ideally, the password should be minimum of 20 characters long.
Change the password of the admin account to a random string of letters and numbers and make it at least 14 characters long.
You can access the console of your router from any device connected to the network. Most Wi-Fi manufacturers set up the administrator account on routers with the same username and password for every piece of equipment they sell. This is different from simply connecting to the network; it grants you control over the network configuration. With a bit of know-how, anyone connected to the router can guess or Google its login credentials. This makes you vulnerable to a hacker or a young overachiever.
The default username and password may be printed in a booklet that came in the box with the router or you may be able to find it in the support pages on the Wi-Fi manufacturer’s website. It might even be displayed on the login screen for the router. If you can’t find the username and password anywhere try sys/admin, system/admin, admin/admin, user/user, system/password, and admin/password for the username/password combination.
Change the network name
Change the SSID so that it doesn’t give away the router brand or model. Don’t choose an identifier that includes your name, address, or phone number. Don’t use any other personal information in the name.
Strengthen Wi-Fi encryption
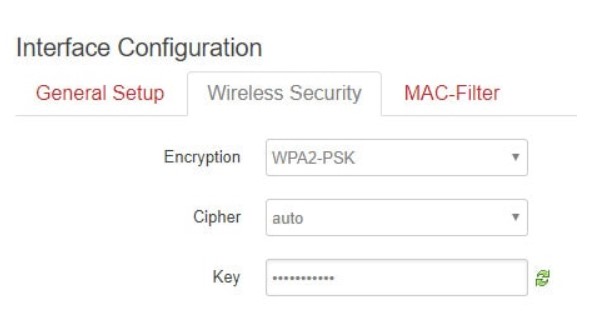 You can change the Wi-Fi encryption in the router console. The AES encryption option often appears in a second pick-list. After you choose WPA2 in the first field, you can select AES in the second field.
You can change the Wi-Fi encryption in the router console. The AES encryption option often appears in a second pick-list. After you choose WPA2 in the first field, you can select AES in the second field.
4. Phishing, Spoof & Spam Emails
Avoid clicking links in emails from people you do not know. Those could be phishing, spoof & spam emails. Please read the following to get familiarized with these attacks.
Phishing: Phishing is a type of fraud in which a hacker attempts to gather personal information or credentials by impersonating a legitimate brand and sending users to a malicious website. A hacker sends an email that appears to come from Microsoft asking the user to log in to their Office 365 account. When the user clicks on the link in the email, it takes them to a fake Office 365 login page, where their credentials are harvested. With Microsoft branding and logos both in the email and on the phishing page, an untrained user will not recognize the email as a phishing attempt.
Spoofing: Email addresses can be spoofed. Never trust an email based simply on the sender name. Cybercriminals have many methods to disguise emails. They understand how to trick their victims into thinking a sender is legitimate, when the email is really coming from a malicious source. With display name spoofing, the phisher uses a legitimate company name as the email sender, such as microsoftsupport@microsoft.com, but the email underneath is a random address like xyz@yahoo.com.
5. Perform a full scan of external drives, pen drives & SD cards
Always scan removal devices such as external drives, pen drives & etc., before you open.
6. Windows update
Open Windows Update by clicking the Start button in the lower left corner. In the search box, type Update, and then, in the list of results, click either Windows Update or Check for updates.
Click the Check for updates button and then wait while Windows looks for the latest updates for your computer.
If you see a message telling you that important updates are available, or telling you to review important updates, click the message to view and select the important updates to install.
In the list, click the important updates for more information. Select the check boxes for any updates that you want to install, and then click OK.Click Install updates.
7. Lock your laptop
Lock your laptop when you aren’t working to avoid any unintentional misuse of office resources.To lock PC type “Windows Key + L”
8. Visit only trusted sites
Visit only trusted sites and always check for https or the lock sign while browsing.
About OM Group Inc
OM Group solves complex government IT mission challenges via digital transformation initiatives, including Cloud Migration, IT Modernization, Robotic Process Automation, Agile DevSecOps, & Enterprise Systems Integration. Our Research and Development Team thinks steps ahead for our clients, delivering practical innovations to solve pressing needs. We bring deep understanding of DoD network and environments, anchored by modern, lean, commercial best practices rooted in CMMI DEV/SVC L3, ISO 9001, and ISO 27001 standards. 8a/WOSB
